What is Vulnerability Management?
It might sometimes get confused with Pen testing but Vulnerability management are totally different things. They are both equally critical for organizations because they serve the purpose of going hand in hand of identifying risk and making an organization’s systems more secure. For example, VM is like going around your own house and checking the locks on every single door, window, or any compartment worth securing. You would want to check each one by jiggling the latch and pulling the latch to check if the lock is secured and hasn’t been tampered with. If, you so happen to find a door without a lock or it doesn’t work it seems to be tampered with you as the Vulnerability assessor deciding its worth noting and pursuing action to harden your physical security. Pen testing on the other hand is like hiring an outside firm to try to break in from the outside with inside knowledge given or without and try to break in to your home through as many means necessary to find weaknesses in your vicinity. If they get access they will try to see what they can find and get access to and get back to you with everything they were able to find.
Using this analogy you can probably see why a vulnerability assessment is essential because it would make the job of the hired pen tester much more difficult. That’s… IF we fixed any of our found vulnerabilities and took action to secure the network than yes! There are companies I hear that that do VM alone, without frequent pen tests to back it up or too few. Some other companies I also hear who do both strategies and won’t do anything about the information found for who knows what reason! I can imagine it can be costly to perform. I see now how it can be an issue if all the work is being done to try to spot weaknesses in ones network without putting in the work of implementation in securing ones network
I’m going to give you a pretty concise definition of what exactly vulnerability management is exactly by a leading industry tool called Rapid7: “VM is a continuous cybersecurity process that includes identifying, evaluating, treating, and reporting software and network vulnerabilities.” I like this definition because its short and straight to the point of what VM is. It is not a one and done thing its a continous process that needs to be constantly be tweaked and tuned for your organizations environment. How I would explain it in my own words, ” the process in which an enterprise does its own due diligence on it’s own network and systems by using software and intelligent personal to attempt to find weaknesses and if found, work diligently to patch them.
Vulnerability vs Threat vs Risk
Knowing the difference between these three terms is crucial for Vulnerability Management.
-Vulnerability:
A vulnerability is basically a weak spot within an asset in your environment. Basically a bad actor can use this open door to gain access. Software and system vulnerabilities are usually named CVEs (common vulnerability and exposures). They are maintained and distributed by an organization called MITRE in which they’re a non-profit that is funded by CISA.( Gov agency)
The purpose of MITRE CVE program is to catalog, standardize, and disclose publicly known vulnerabilities with anything running on a computer. Think of it as a national recall list for software.
Threat:
A threat is a potential to harm a system or an entity. There a three types of threats:
Natural Threats synonymous with acts of god; for example natural disasters like floods, tornados, and hurricanes etc.
Unintentional Threats are mostly the fault of human error. Misconfigurations on devices and code are the most common type of unintentional threats.
Intentional Threats are done on purpose with the intention of garnering financial gain, reputation tarnishing, and quite possibly just to troll.
Risk:
Threat Likelihood x Vulnerability Impact = Risk. For example let’s say you live in the middle of nowhere and you find yourself running late for work. You rush out and leave the door open leaving a huge vulnerability but since there’s not a low foot traffic in your neighborhood the likely hood of someone malicious spotting that you left your door unlocked is low. Making it still in my opinion very HIGH risk because all it takes is for one curious individual to walk up to your door and break in very easily! OWASP ( Open Web Application Security Project) has a nice chart illustrating what we are talking about.
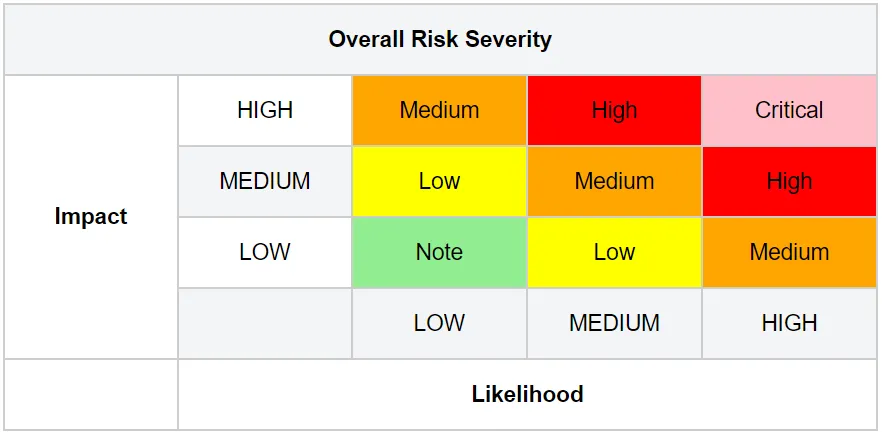
For the example shown above, when we map are low likelihood with our high vulnerability impact we get a MEDIUM risk. Now, lets say we live in an apartment building with a ton of foot traffic and we are late for work again! We rush out and leave the door open again… The likelihood of someone curiously attempt to open your door is way HIGHER. The vulnerability is still the same, a bad actor can still open the door easily still HIGH impact. Now, the risk calculation is HIGH likelihood x HIGH IMPACT = CRITICAL Risk severity! We must consider our environment as well. In our earlier example of our own home we assessed our vulnerabilities and didn’t really consider a insane threat of getting hit by artillery shells, weapons, bullets etc… because what are the odds of that happening! Lets say we are a secret government facility and have secret weapons, labs, date etc.. to protect. In our vulnerability assessment of the facility we would need to consider external environmental factors as well because our likelihood is HIGH. That’s why knowing your assessing your environment and threats is crucial in helping asses your risk.
The Vulnerability Management Process
How does one manage these risks? Here’s a diagram showcasing the Gartner VM process:
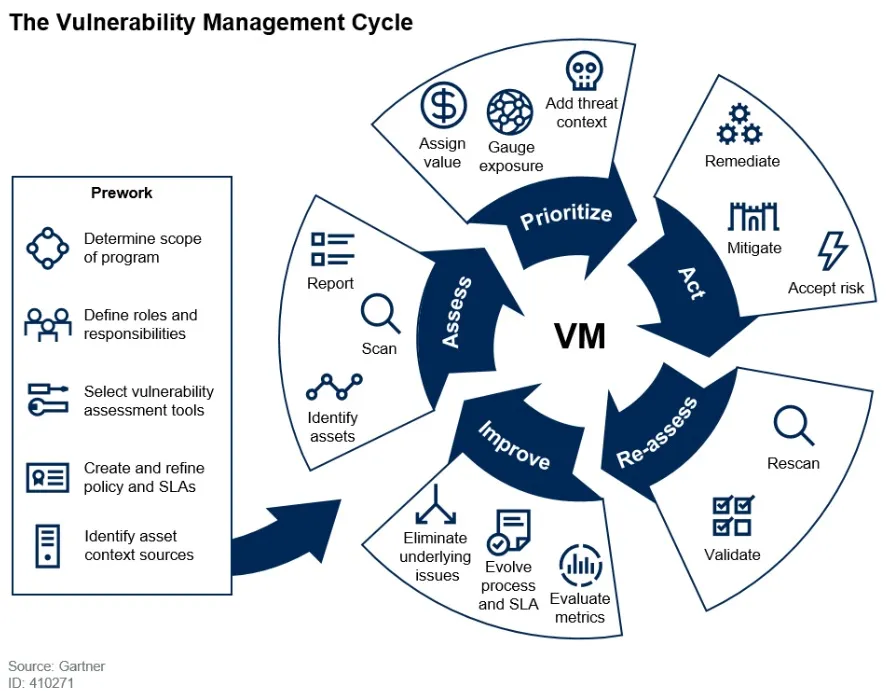
We are going to go into a little bit of each step of the diagram process:
Asses
The assessment phase is finding out what assets we have, what’s wrong with them, and documenting those findings. It is done in the following order:
Identify Assets:
It’s important to go through thoroughly what inventory we have to secure. Much easier said than done because some organizations might not have their stuff together and might or might not have a inventory list or lack of network diagrams. Even if they do, it might be outdated! They are the most common hurdles for the assessment phase but needed to conduct our vulnerability scan.
Scan:
A vulnerability scan is at the heart of getting to the bottom of what’s cracking with your network. It is recommended to run authenticated scans against our devices therefore; allowing us the ability to get the most accurate assestment by allowing the scanner to interrogate parts of the system that require root access. There are many free and paid tools out there. All of which are programmed to scan devices (either via a network scan or local installed agents) for known CVEs.
- Free: OpenVAS, Nessus Essentials, Vuls.io
- Paid: Qualys, Tenable, Nexpose
Report:
Reporting is vital to the VM process, if it’s not documented to excruciating detail it can be ignored making the whole process a total waste.
Priortize
There are only so many hours in the day and only so much patching can be done during that time frame. We must prioritize and take advantage of our available resources and must draw the line on what vulnerabilities are critical first and put all minors ones at the bottom of the list. To do this adequately we must consider the following:
Assign value:
We can prioritize assets by assigning values to our assets. External public facing assets should be the highest priority asset. Second, should be the “Crown Jewels” (sensitive customer data, intellectual property, etc.).
Gauge exposure:
This is a very critical step in asset remediation. Exposure estimating is assessing the potential for one to be a target. This could be based on technology, reputation, or external factors. For example there is this vulnerability called Log4shell. Basically what it does is, the logging component of Apache ( popluar webserver software) was susceptible to a remote code execution exploit. If your environment uses Apache and specifically Log4j for webserver logging, your exposure would be much greater than another environment running on IIS(Microsoft webserver software that doesn’t leverage the Log4j component). It is important to run the appropriate response to patching said vulnerability by running it on a test environment or if push comes to show downgrading to a invulnerable version might help if there isn’t any know patches by the vendor themselves yet to lower the company’s risk exposure for the meantime.
Add Threat Context:
Threat context is basically threat intel of what’s going on out there in the wild. CISA (Cybersecurity & Infrastructure Security Agency) provides reports(and IoCs- Indicators of Compromise) of on going threat actors and their known campaigns. There is also other free and paid resources. Threat context are useful to readjust our assessment of vulnerabilities on certain assets. If it’s not targeting an important asset to the organization it will get bumped down the priority list.
- It’s like saying a neighborhood community member posted on the ring camera saying burglars have been walking up to homes checking to see if we leave the doors unlocked. Your first reaction should be to want to make sure to close the doors when we leave our homes.
Act
So once we have a list of vulnerabilities we would love to address them all but sometimes it can be difficult for an organization. Sometimes it may be cost effective to address all vulnerabilities it might take too much time and money to address all vulnerabilities leaving us with the task of prioritizing the most critical only, or none at all. Your enterprise might be blessed with a well funded and staffed organization and your able to patch them all!
Remediate:
Applying the full fix to address the issue or removing it from your environment all together is called remediating the risk. That’s what I meant earlier by applying patches iin at test environment was basically remediation tactics.
Mitigate:
Mitigation of a vulnerability involves applying a partial fix or a workaround that addresses all or some underlying issues. For example, if a Windows RDP (remote desktop protocol) vulnerability is disclosed, a mitigation could be to turn off RDP and close port 3389 (standard port). The mitigation didn’t fix the vulnerability but instead removed the threat vector. Just like in our applying patches example we could downgrade to a previous version to remove the risk of the vulnerable update hindering our systems is also a great example of mitigation.
Accept Risk:
DO NOTHING & ACCEPT YOUR FATE! Seriously, though a lot of thought is put into accepting risk by assuring stakeholders that certain systems will stay vulnerable despite the potential risk and threats. Typically a remediation plan is put in place for future fixes is required/recommended when accepting risk. This is done to not lose visibility of said risks.
Re-asses
After remediation occurs, the next step is to verify. A common term used in cyber is “Trust… but verify.” Additional scans are performed to ensure the remediation’s applied actually fixed the vulnerability. Some patches might require additional configurations or a reboot to apply changes to resolve the issue.
Improve
The last step in the VM cycle. This is all about lessons learned. What worked well, what didn’t what our pain points in the process, what people/processes/products are needed to make it easier in the future.
Evaluate metric:
If you are performing VM in any sized environment, you’ll want some level of metric. Open/closed vulnerability scans by severity is a simple one. Another could be the MTTR (mean time to remediation) which details how long it takes to solve a vulnerability after it has been found. Larger enterprises have different reporting requirements, that needs to be taken into account.
Evolve Process and SLA (service level agreement):
Identify ways to do things faster, better and cheaper. If there are hiccups in the VM process try to fix them by implementing additional resources, better processes, or new/advanced tools.
Eliminate Underlying Issues:
Act on the areas identified in thee previous steps. You may need longer patching windows or a step in the CI/CD pipeline to address vulnerabilities prior to deploying into production. Opportunities to improve are useless if its just written down and not acted upon ourselves as VM specialists or the organization isn’t keen on it.

Conclusion
It’s quite surprising to learn how overlooked this section of cyber security is overlooked and underfunded. Pen testing is great but having an active and working VM program will increase the security posture of your environment even more! I’ll say both pen testing and vulnerability management go hand and hand seamlessly in securing your environment! This concludes our comprehensive guide to vulnerability management process and each step has more in depth sub steps in which we could go deeper into but the goal for today was to get an introductory grasp of the Vulnerability Management process that every competent organization should always instill an ongoing process. In the future we will set up a home lab and run a VM assessment on our own home network! Till next time, be legendary!