One of the BEST resources in the industry
Yeah, you could use Microsoft Defender to remove malware from your device but as an aspiring professional its best to understand how the malware got their in the first place to prevent it from happening in the future.
The tool that is able to understand this is MITRE ATT&CK Framework:
It is pretty much a life cycle of every potential phase of malware and the ways it does bad things or sets itself up to be malicious.
In this post we will have a basic understanding of:
- What it is
- How it works
- How it relates to malware in the wild
- Some ways that teams use it
MITRE ATT&CK Framework – Everything You Need to Know
Cyber-attack frameworks are often used to defend against attacks on networks and systems. Only a small number of them offer countermeasures because there aren’t many attack-defense frameworks out there. Thus, many professionals themselves don’t know how to defend the network when incidents occur. This is why it’s essential to have a incident response plan/playbook before an attack happens. We will talk about this another day :)The MITRE ATT&CK matrix maps the NIST Cybersecurity framework to the Cyber Threat Dictionary by providing concepts and solutions in response to cyber attacks by handing security professionals quick fixes.
What is MITRE ATT&CK FRAMEWORK?
An open framework called MITRE ATT&CK framework that is used to develop cybersecurity detection and response programs. Pretty much a huge knowledge base of adversarial TTP (Tactics, Techniques, & common knowledge) based on real world observations in the ATT&CK architecture free resource. It helps I can imagine thousands of IT professionals in being compliant by identifying security flaws, assesing risks, and removing vulnerabilities. Sounds exactly like Vulnerability management from our previous post!
ATT&CK also imitates the actions of real attackers. Advanced Persistent Threats (APTs), or malware that operates for a cool minute in a target system without it being noticed are emphasized in ATT&CK. Apts are also used to categorize malware gangs, often being associated with nation state threat actors. Instead of saying ” China Nation State Threat Actor who target Legal and Investment,” we can say instead is APT 19. It may also reference the malware they use instead.
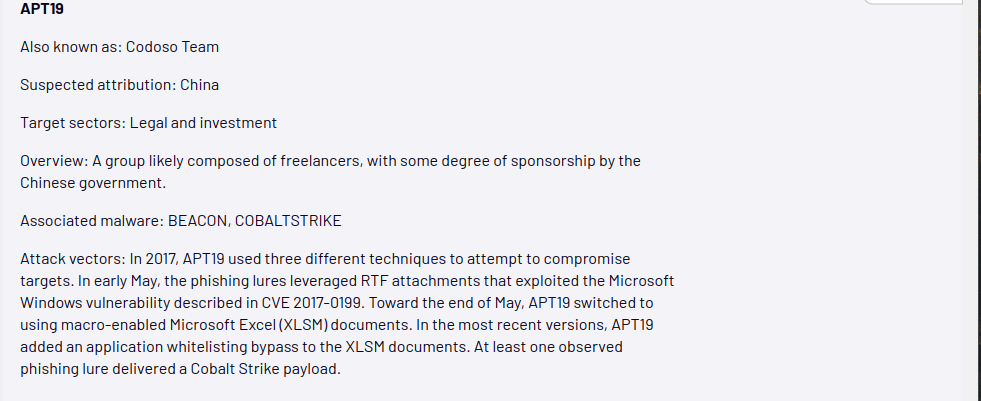
An APT intrusion can prove to be a fatal and expensive blow! They can be in your network for weeks or months without being noticed ex filtrating sensitive data or carry out operations like crypto mining or spam mailing.
What is MITRE ATT&CK’S Goal?
The Mitre cybersecurity knowledge base’s goal is to empower teams to adopt the perspective of the attacker point of view to comprehend more in depth the driving factor why an attacker’s activities and strategies for more comprehensive threat detection and response. This method gives context to each type of attack, enabling blue teams to anticipate an adversary’s behavior and anticipate to respond to attacks swiftly and seamlessly.
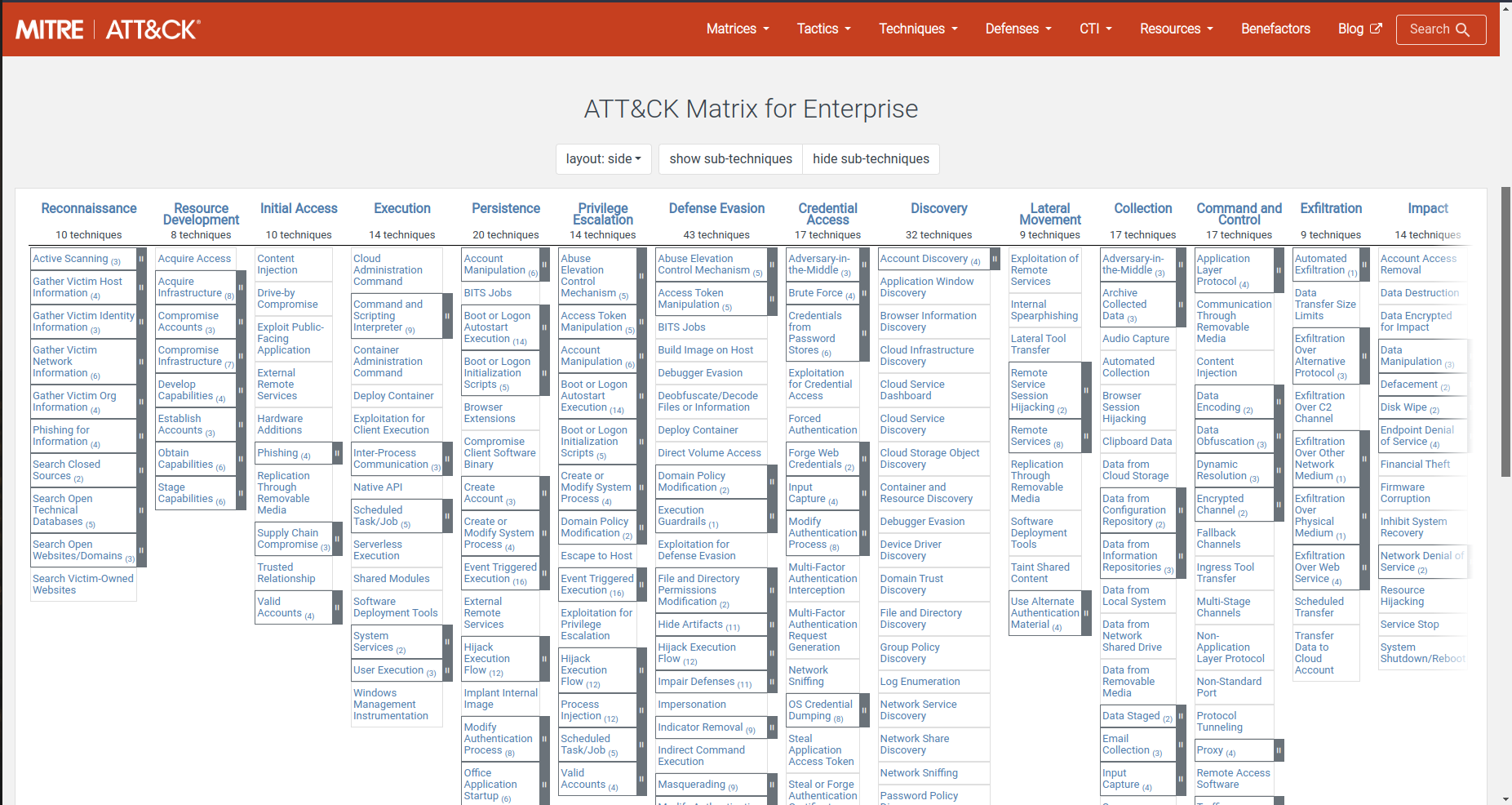
Knowledge of ATT&CK Matrices
Enterprise, mobile, and PRE-ATTACK are three seperate matrices that Mitre has divided into three for ATT&CK. There are tons of strategies and methods that are associated with each subject matter of these matrices.
Techniques and strategies that work with Windows, Linux, and macOS systems make up the Enterprise matrix. Mobile device OS have their own unique strategies and procedures. PRE-ATTACK refers to the strategies and methods used by attackers before attempting to exploit a network or system.
Applications of the MITRE ATT&CK Framework
The MITRE ATT&CK Framework is integrated into several preventative measures:
- Breach and Attack Simulation: This tool can simulate attack scenarios and test their effectiveness of your security implemetations.
- Red and Blue teaming: Red teams can utilize penetration testing to simulate attacks. Blue teams might strengthen their defensive mechanisms by simulating a live attack.
- SOC Maturity Assessment: The SOC Maturity Assesment can asses how well your security operations center (SOC) can identify, assess, and respond to incidents.
- Threat Intelligence Enrichment: By comprehending the profiles and activities of APTs, threat intelligence can be enhanced.
- Vendor Analysis: The efficacy of vendor products varies greatly. ATT&CK offers tools to objectively assess which vendor best meets your needs by comparing product capabilities to combat typical threats.
A robust open-source tool from MITRE ATT&CK makes it possible to categorize the strategies and methods of tons of well known cyber attacks. They’re simple taxonomy of threats defined by MITRE, making it easy for cyber security providers to get involved and share the knowledge. It can greatly enhance cyber security experts to prioritize security incidents that can be mitigated to lower business risk and build a solid strategy for security controls to guard against highly probable attacks.
Understanding MITRE ATT&CK Techniques, Tactics, & Procedures
ATT&CK Tactics
The MITRE ATT&CK framework compromises of 11 tactics that explain the ratioanale for an adversary’s strategy and predicts the attacker’s goal. Each tactic’s need for security coverage is given equal weight of importance under ATT&CK.
These tactics are:
- Initial Access
- Discovery
- Lateral Movement
- Collection
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Exfiltration
- Execution
- Impact
ATT&CK Techniques
The “how” an enemy accomplishes a goal- the action they take to obtain their goal — is through ATT&CK Techniques. The framework thoroughly explains how approaches are applied and why security teams must dive deep to countermeasure.
MITRE ATT&CK and its Core Impact
Security teams can evaluate their security environment by using MITRE ATT&CK Core Impact. It is an automated pen test tool that finds exploits security flaws. The testing engagement is compliments by the MITRE ATT&CK Framework. Another similiar product that is similiar is Metasploit Pro. In the future we will cover it 🙂 for the time being its pretty cool that pen testing can be automated even though it might rack up a pretty penny. I can see it being implemented in a enterprise environment.
Report Produced Using NIST 800 Navigator
This paper provides a modified JSON output for enterprises that seek to align their actions with ATT&CK and NIST’s catalog of security and privacy controls aka NIST 800-53.
The Navigator Report by ATT&CK
This report employs the MITRE layer to categorize and prioritize risk based on the methods used during an engagement. Additionally, it offers the choice of exporting data in ATT&CK Navigator JSON format.
How can Organizations Benefit from MITRE ATT&CK?
The MITRE ATT&CK architecture has many benefits for organizations. To test and validate existing cybersecurity measures against APTs, malware, etc.
Campaigns centered on ATT&CK can simplify monitoring threats, identifying patterns, and assessing how well existing vendor products are doing. ATT&CK can also be used to build and test behavioral analytics to identify insiders hostile behavior and evaluate the tools, monitoring, and mitigations of current defenses across and organization’s enterprise.
The framework also can be an indicator of how a SOC detects, evaluates, and reacts to intrusion. Lastly, ATT&CK helps understand and document adversary group profiles from an unbiased behavioral insight.
Final Comments
For Enterprises looking to stay one step ahead of attackers, the MITRE Enterprise ATT&CK Framework is a valuable tool. The MITRE ATT&CK taxonomy has provided defenders a roadmap for detecting threats, assessing risk, and taking steps to mitigate those threats by offering a curated and complete list of tactics and actions to implement. That is everything we needed to learn about the MITRE ATT&CK framework! Cheers, and don’t forget to be legendary!